
DEVELOP AND NURTURE TALENTS OF THE WORLD
QUANTIFY AND ENHANCE VALUE OF THE INDUSTRY
DEVELOP AND NURTURE
TALENTS OF THE WORLD
QUANTIFY AND ENHANCE
VALUE OF THE INDUSTRY
































































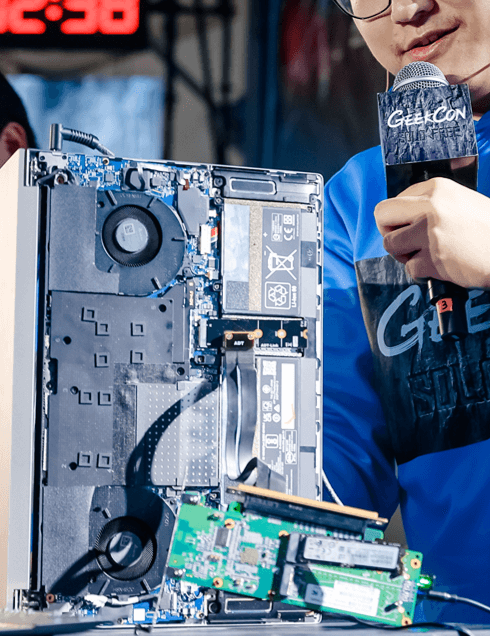
1 GEEKCON organizing committee (hereinafter referred to as "the committee") recognizes the technical capability of the winner individually, but doesn't acknowledge that it represents the capability of the winner's working organization.
2 We recognize and promote the comprehensive assessment of vulnerability exploitation capabilities and mitigation mechanisms from a confrontational perspective, and do not endorse the judgement of security levels of the target products involved in the event based on a single dimension or non-quantitative dimension.
3 The committee firmly follows the Responsible Disclosure principle. The committee and contestant commit not to disclose any details to third-party before manufactures fix the issues.
4 The committee advocates and encourages in-depth knowledge sharing and communication, but firmly opposes any speech and behavior that violates laws and regulations or infringes on the rights of others.
5 The committee guarantees that the participants' personal information will not be disclosed to third-party or used for commercial activities without their agreement and authentication.
6 We will set up awards and honors based on the research efforts, technical breakthrough, and technical innovation of the projects. As the top 1 security geek IP operator in China, we always advocate a reward mechanism that emphasizes both honor and moderate bounty, encouraging more geeks to participate in technical innovation and knowledge sharing.